Understanding Cisco Cybersecurity Fundamentals (SECFND):210-250 exam. Share the latest 210-250 exam dumps and Practice test questions for free. Real and effective exam questions and answers. 210-250 pdf online Download.
Micvce share 30 Practice test questions for FREE! Get the full 210-250 exam dumps: https://www.leads4pass.com/210-250.html (Total questions:1082 Q&A)
[PDF] Free Cisco 210-250 pdf dumps download from Google Drive: https://drive.google.com/open?id=1Avb4ycH4Xh7EOgTt3TnD0ECe_gtPxkcQ
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
210-250 SECFND – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/secfnd.html
Latest effective Cisco 210-250 Exam Practice Tests
QUESTION 1
Which protocol is primarily supported by the third layer of the Open Systems Interconnection reference model?
A. HTTP/TLS
B. IPv4/IPv6
C. TCP/UDP
D. ATM/ MPLS
Correct Answer: B
QUESTION 2
A firewall requires deep packet inspection to evaluate which layer?
A. application
B. Internet
C. link
D. transport
Correct Answer: A
QUESTION 3
Which three statements about host-based IPS are true? (Choose three.)
A. It can view encrypted files.
B. It can have more restrictive policies than network-based IPS.
C. It can generate alerts based on behavior at the desktop level.
D. It can be deployed at the perimeter.
E. It uses signature-based policies.
F. It works with deployed firewalls.
Correct Answer: ABC
QUESTION 4
What are two Features of NGFW:
A. Data Mining,
B. Host Based AV
C. Application visibility and control
D. SIEM
E. IDS
Correct Answer: CE
QUESTION 5
Which hash algorithm is the weakest?
A. SHA-512
B. RSA 4096
C. SHA-1
D. SHA-256
Correct Answer: C
QUESTION 6
Which definition of the virtual address space for a Windows process is true?
A. actual physical location of an object in memory
B. set of virtual memory addresses that it can use
C. set of pages that are currently resident in physical memory
D. system-level memory protection feature that is built into the operating system
Correct Answer: B
QUESTION 7
Which actions can a promiscuous IPS take to mitigate an attack? Choose three
A. Denying Frames
B. Resetting the TCP Connection
C. Requesting host blocking
D. Modifying packets
E. Denying packets
F. Requesting connection blocking
Correct Answer: BCF
QUESTION 8
Which three options are types of Layer 2 network attack? (Choose three.)
A. ARP attacks
B. brute force attacks
C. spoofing attacks
D. DDOS attacks
E. VLAN hopping
F. botnet attacks
Correct Answer: ACE
QUESTION 9
While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by
modifying the IP header.
Which option is making this behavior possible?
A. TOR
B. NAT
C. encapsulation
D. tunneling
Correct Answer: B
QUESTION 10
What type of algorithm uses the same key to encrypt and decrypt data?
A. A symmetric algorithm
B. An asymmetric algorithm
C. A public key infrastructure algorithm
D. An IP security algorithm
Correct Answer: A
QUESTION 11
In which context is it inappropriate to use a hash algorithm?
A. Telnet logins
B. Verifying file integrity
C. SSH logins
D. Digital signature verification
Correct Answer: A
QUESTION 12
Which security monitoring data type requires the most storage space?
A. full packet capture
B. transaction data
C. statistical data
D. session data
Correct Answer: A
QUESTION 13
Refer to the exhibit.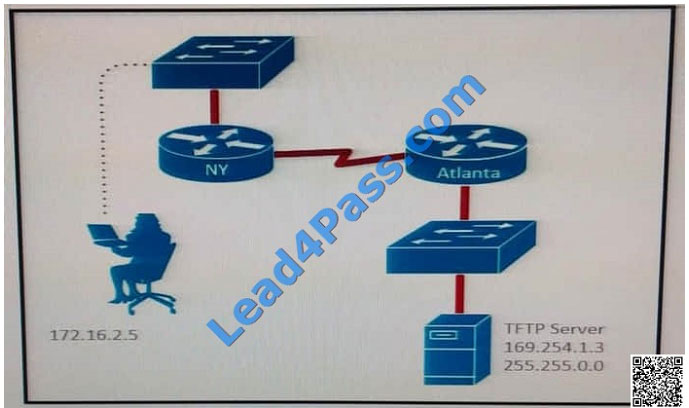 A TFTP server has recently been installed in the Atlanta office. The network administrator is located in the NY office and
A TFTP server has recently been installed in the Atlanta office. The network administrator is located in the NY office and
has attempted to make a connection to the TFTP server. They are unable to back up the configuration file and Cisco
IOS
of the NY router to the TFTP server.
Which cause of this problem is true?
A. The TFTP server cannot obtain an address from a DHCP Server.
B. The TFTP server has an incorrect IP address.
C. The network administrator computer has an incorrect IP address
D. The TFTP server has an incorrect subnet mask.
Correct Answer: A
QUESTION 14
Which of the following access control models use security labels to make access decisions?
A. Role-based access control (RBAC)
B. Mandatory access control (MAC)
C. Identity-based access control (IBAC)
Correct Answer: B
QUESTION 15
Which of the following are some useful reports you can collect from Cisco ISE related to endpoints? (Select all that
apply.)
A. Web Server Log reports
B. Top Application reports
C. RADIUS Authentication reports
D. Administrator Login reports
Correct Answer: ABD
QUESTION 16
Which data can be obtained using NetFlow?
A. session data
B. application logs
C. network downtime
D. report full packet capture
Correct Answer: A
QUESTION 17
What event types does FMC record?
A. standard common event logs types
B. successful login event logs
C. N/A
Correct Answer: C
QUESTION 18
What does the sum of the risks presented by an application represent for that application?
A. Application attack surface
B. Security violation
C. Vulnerability
D. HIPPA violation
Correct Answer: A
QUESTION 19
Which directory is commonly used on Linux systems to store log files, including syslog and apache access logs?
A. /etc/log
B. /root/log
C. /lib/log
D. /var/log
Correct Answer: D
QUESTION 20
Which NTP command configures the local device as an NTP reference clock source?
A. ntp peer
B. ntp broadcast
C. ntp master
D. ntp server
Correct Answer: C
QUESTION 21
An attacker installs a rogue switch that sends superior BPDUs on your network.
What is a possible result of this activity?
A. The switch could offer fake DHCP addresses.
B. The switch could become the root bridge.
C. The switch could be allowed to join the VTP domain
D. The switch could become a transparent bridge.
Correct Answer: B
QUESTION 22
Based on which statement does the discretionary access control security model grant or restrict access?
A. discretion of the system administrator
B. security policy defined by the owner of an object
C. security policy defined by the system administrator
D. role of a user within an organization
Correct Answer: B
QUESTION 23
Which definition of a Linux daemon is true?
A. Process that is causing harm to the system by either using up system resources or causing a critical crash.
B. Long ?running process that is the child at the init process
C. process that has no parent process
D. process that is starved at the CPU.
Correct Answer: B
QUESTION 24
Which two terms are types of cross site scripting attacks? (Choose two )
A. directed
B. encoded
C. stored
D. reflected
E. cascaded
Correct Answer: CD
QUESTION 25
Which two features must a next generation firewall include? (Choose two.)
A. data mining
B. host-based antivirus
C. application visibility and control
D. Security Information and Event Management
E. intrusion detection system
Correct Answer: CE
QUESTION 26
Which of the following is true about heuristic-based algorithms?
A. Heuristic-based algorithms may require fine tuning to adapt to network traffic and minimize the possibility of false
positives.
B. Heuristic-based algorithms do not require fine tuning.
C. Heuristic-based algorithms support advanced malware protection.
D. Heuristic-based algorithms provide capabilities for the automation of IPS signature creation and tuning.
Correct Answer: A
QUESTION 27
which security principle is violated by running all processes as root/admin
A. RBAC
B. Principle of least privilege C. Segregation of duty
Correct Answer: B
QUESTION 28
What Linux commands show the process for all users?
A. ps –a
B. ps –u
C. ps –d
D. ps –m
Correct Answer: A
QUESTION 29
Where does routing occur within the DoD TCP/IP reference model?
A. application
B. internet
C. network
D. transport
Correct Answer: B
QUESTION 30
Which term represents the chronological record of how evidence was collected- analyzed, preserved, and transferred?
A. chain of evidence
B. evidence chronology
C. chain of custody
D. record of safekeeping
Correct Answer: C
Share 30 of the latest and effective 210-250 dumps and Practice test questions for free,100% real and effective exam questions and answers! Get the full 210-250 exam dumps:https://www.leads4pass.com/210-250.html
(Total questions:1082 Q&A)
[PDF] Free Cisco 210-250 pdf dumps download from Google Drive: https://drive.google.com/open?id=1Avb4ycH4Xh7EOgTt3TnD0ECe_gtPxkcQ
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
leads4pass Promo Code 12% Off

related: https://www.micvce.com/100-pass-latest-cisco-ccnp-collaboration-300-075-dumps/