Implementing Cisco Cybersecurity Operations (SECOPS) v1.0:210-255 exam. Share the latest 210-255 dumps and Practice test questions for free. Real and effective exam questions and answers. 210-255 pdf online Download.
Micvce share 30 Practice test questions for FREE! Get the full 210-255 exam dumps: https://www.leads4pass.com/210-255.html (Total questions:170 Q&A)
[PDF] Free Cisco 210-255 pdf dumps download from Google Drive: https://drive.google.com/open?id=1DvJqIWfL52ROsKHiVgNW44JumpzOCCj_
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
210-255 SECOPS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/secops.html
Latest effective Cisco 210-255 Exam Practice Tests
QUESTION 1
Drag and drop the type of evidence from the left onto the correct descnption(s) of that evidence on the right.
Select and Place: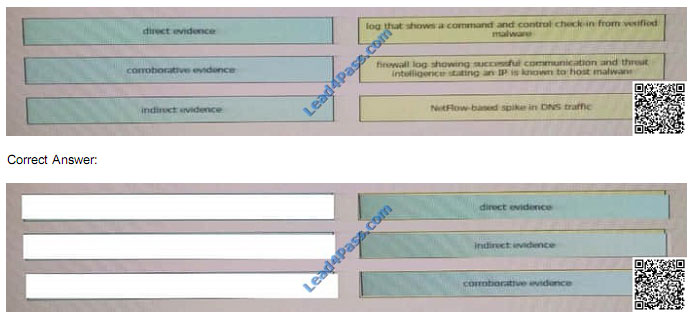
QUESTION 2
Which CVSSv3 metric value increases when the attacker is able to modify all files protected by the vulnerable
component?
A. confidentiality
B. integrity
C. availability
D. complexity
Correct Answer: B
QUESTION 3
How is confidentiality defined in the CVSS v3.0 framework?
A. confidentiality of the information resource managed by person due to an unsuccessfully exploited vulnerability
B. confidentiality of the information resource managed by a person due to a successfully vulnerability
C. confidentiality of the information resources managed by a software component due to a successfully exploited
vulnerability
D. confidentiality of the information resource managed by a software component due to an unsuccessfully exploited
vulnerability
Correct Answer: C
QUESTION 4
Which Cyber Kill Chain Model category does attacking a vulnerability belong to?
A. Exploitation
B. Action on Objectives
C. Installation
D. Delivery
Correct Answer: A
QUESTION 5
Which of the following is the team that handles the investigation, resolution, and disclosure of security vulnerabilities in
vendor products and services?
A. CSIRT
B. ICASI
C. USIRP
D. PSIRT
Correct Answer: D
QUESTION 6
When incident data is collected, it is important that evidentiary cross-contamination is prevented. How is this
accomplished?
A. by allowing unrestricted access to impacted devices
B. by not allowing items of evidence to physically touch
C. by ensuring power is removed to all devices involved
D. by not permitting a device to store evidence if it is the evidence itself.
Correct Answer: D
QUESTION 7
Which CSIRT category provides incident handling services to their parent organization such as a bank, a manufacturing
company, a university, or a federal agency?
A. internal CSIRT
B. national CSIRT
C. coordination centers
D. analysis centers
E. vendor teams
F. incident response providers
Correct Answer: A
QUESTION 8
What is a listening port?
A. A port that remains open and waiting for incoming connections
Correct Answer: A
QUESTION 9
Refer to the exhibit.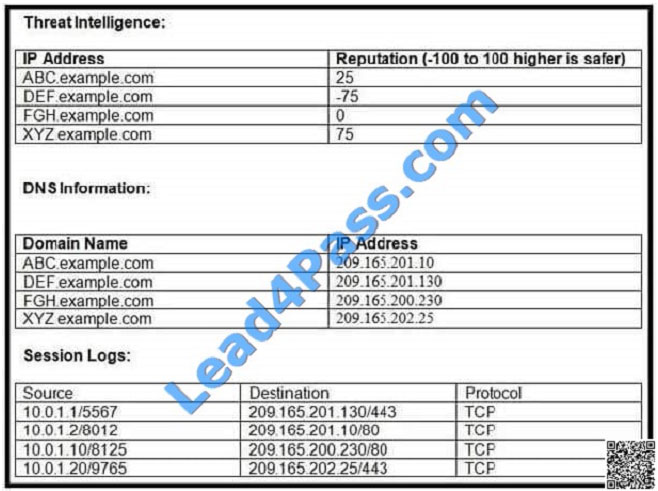 Which host is likely connecting to a malicious site?
Which host is likely connecting to a malicious site?
A. 10.0.1.10
B. 10.0.1.1
C. 10.0.1.2
D. 10.0.1.20
Correct Answer: B
QUESTION 10
Which component of the NIST SP800-61 r2 incident handling strategy reviews data?
A. preparation
B. detection and analysis
C. containment, eradication, and recovery
D. post-incident analysis
Correct Answer: D
QUESTION 11
Which source provides reports of vulnerabilities in software and hardware to a Security Operations Center?
A. Analysis Center
B. National CSIRT
C. Internal CSIRT
D. Physical Security
Correct Answer: C
QUESTION 12
Which of the following are the three broad categories of cybersecurity investigations?
A. Public, private, and individual investigations
B. Judiciary, private, and individual investigations
C. Public, private, and corporate investigations
D. Government, corporate, and private investigations
Correct Answer: A
QUESTION 13
Refer to the exhibit. Which type of log is this an example of? A. syslog
A. syslog
B. NetFlow log
C. proxy log
D. IDS log
Correct Answer: D
QUESTION 14
During which phase of the forensic process are tools and techniques used to extract the relevant information from the
collective data?
A. examination
B. reporting
C. collection
D. investigation
Correct Answer: A
Examinations involve forensically processing large amounts of collected data using a combination of automated and
manual methods to assess and extract data of particular interest, while preserving the integrity of the data. Forensic
tools and techniques appropriate to the types of data that were collected are executed to identify and extract the
relevant information from the collected data while protecting its integrity. Examination may use a combination of
automated tools and manual processes.
QUESTION 15
You see confidential data being exfiltrated to an IP address that is attributed to a known Advanced Persistent Threat
group. Assume that this is part of a real attach and not a network misconfiguration. Which category does this event fall
under as defined in the Diamond Model of Intrusion?
A. reconnaissance
B. weaponization
C. delivery
D. action on objectives
Correct Answer: D
QUESTION 16
Refer to the exhibit. Which application protocol is in this PCAP file?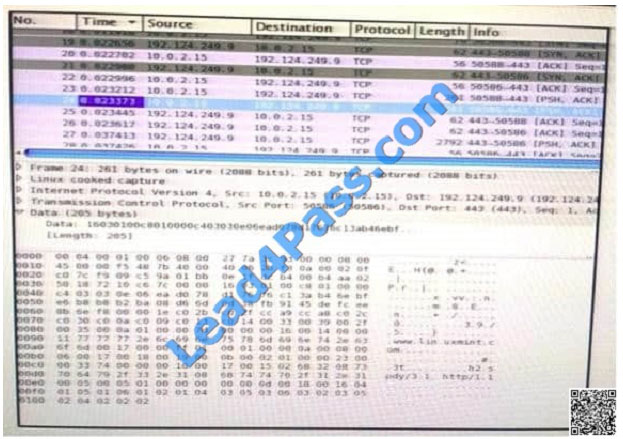 A. TCP
A. TCP
B. SSH
C. HTTP
D. SSL
Correct Answer: D
QUESTION 17
Which statement about collecting data evidence when performing digital forensics is true?
A. Allowing unrestricted access to impacted devices
B. Not allowing items of evidence to be physically touch
C. Powering off the device after collecting the data
D. It must be preserved and integrity checked
Correct Answer: D
QUESTION 18
Which identifies both the source and destination location?
A. IP address
B. URL
C. ports
D. MAC address
Correct Answer: A
QUESTION 19
Which statement about threat actors is true?
A. They are any company assets that are threatened.
B. They are any assets that are threatened.
C. They are perpetrators of attacks.
D. They are victims of attacks.
Correct Answer: C
QUESTION 20
Which option is a misuse variety per VERIS enumerations?
A. snooping
B. hacking
C. theft
D. assault
Correct Answer: B
QUESTION 21
Which of the following is an example of a coordination center?
A. Cisco PSIRT
B. Microsoft MSRC
C. CERT division of the Software Engineering Institute (SEI)
D. FIRST
Correct Answer: C
QUESTION 22
Which of the following is one of the main goals of the CSIRT?
A. To configure the organization\\’s firewalls
B. To monitor the organization\\’s IPS devices
C. To minimize and control the damage associated with incidents, provide guidance for mitigation, and work to prevent
future incidents
D. To hire security professionals who will be part of the InfoSec team of the organization.
Correct Answer: C
QUESTION 23
According to NIST SP800-86, which action describes volatile data collection?
A. collection of data before a system reboot
B. collection of data that contains malware
C. collection of data during a system reboot
D. collection of data after a system reboot
Correct Answer: A
QUESTION 24
Which of the following is not true regarding the use of digital evidence?
A. Digital forensics evidence provides implications and extrapolations that may assist in proving some key fact of the
case.
B. Digital evidence helps legal teams and the court develop reliable hypotheses or theories as to the committer of the
crime or threat actor.
C. The reliability of the digital evidence is vital to supporting or refuting any hypothesis put forward, including the
attribution of threat actors.
D. The reliability of the digital evidence is not as important as someone\\’s testimony to supporting or refuting any
hypothesis put forward, including the attribution of threat actors.
Correct Answer: D
QUESTION 25
Which two useful pieces of information can be collected from the IPv4 protocol header? (Choose two.)
A. UDP port which the traffic is destined
B. source IP address of the packet
C. UDP port from which the traffic is sourced
D. TCP port from which the traffic was source
E. destination IP address of the packet
Correct Answer: BE
QUESTION 26
Which of the following is not an example of reconnaissance?
A. Searching the robots.txt file
B. Redirecting users to a source and scanning traffic to learn about the target
C. Scanning without completing the three-way handshake
D. Communicating over social media
Correct Answer: B
QUESTION 27
What is NAC?
A. Non-Admin Closure
B. Network Access Control
C. Nepal Airline Corporations
D. Network Address Control
Correct Answer: B
QUESTION 28
What are two security goals of data normalization? (Choose two.)
A. purge redundant data
B. reduce size of data on disk
C. increase data exposure
D. maintain data integrity
E. create data for abstraction
Correct Answer: AD
QUESTION 29
Which event artifact can be used to identify HTTP GET requests for a specific file?
A. HTTP status code
B. TCP ACK
C. destination IP
D. URI
Correct Answer: D
QUESTION 30
Drag and Drop
Built inbound TCP connection 463879 for outside: (25.238.89.53/14846) to DMZ: WWW_Server/80 (198.52.1.50/80)
Select and Place: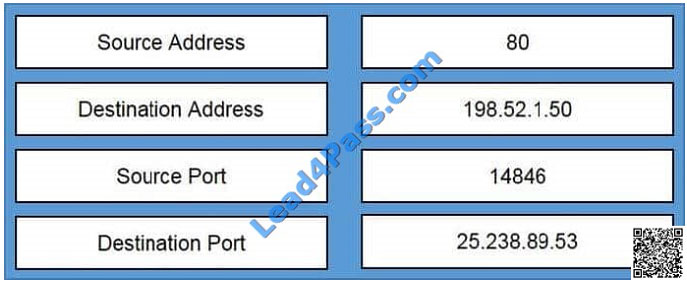 Correct Answer:
Correct Answer: 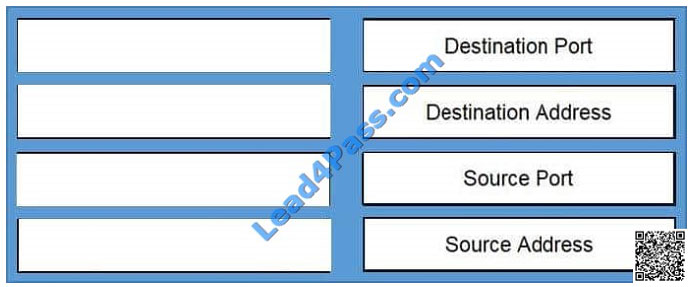
Share 30 of the latest and effective 210-255 exam dumps and Practice test questions for free,100% real and effective exam questions and answers! Get the full 210-255 exam dumps:https://www.leads4pass.com/210-255.html
(Total questions:170 Q&A)
[PDF] Free Cisco 210-255 pdf dumps download from Google Drive: https://drive.google.com/open?id=1DvJqIWfL52ROsKHiVgNW44JumpzOCCj_
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
leads4pass Promo Code 12% Off

related: https://www.micvce.com/helpful-newest-cisco-ccdp-300-101-dumps/