Latest Cisco CCNA Cyber Ops 210-255 exam Dumps Practice Test – Micvce
Implementing Cisco Cybersecurity Operations (SECOPS) v1.0:210-255 exam. Share the latest 210-255 dumps and Practice test questions for free. Real and effective exam questions and answers. 210-255 pdf online Download.
Micvce share 30 Practice test questions for FREE! Get the full 210-255 exam dumps: https://www.leads4pass.com/210-255.html (Total questions:170 Q&A)
[PDF] Free Cisco 210-255 pdf dumps download from Google Drive: https://drive.google.com/open?id=1DvJqIWfL52ROsKHiVgNW44JumpzOCCj_
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
210-255 SECOPS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/secops.html
Latest effective Cisco 210-255 Exam Practice Tests
QUESTION 1
Drag and drop the type of evidence from the left onto the correct descnption(s) of that evidence on the right.
Select and Place: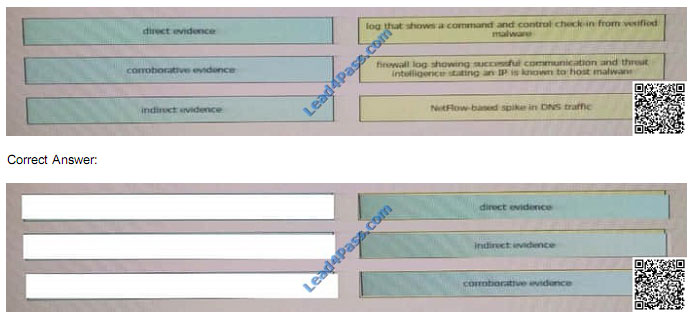
QUESTION 2
Which CVSSv3 metric value increases when the attacker is able to modify all files protected by the vulnerable
component?
A. confidentiality
B. integrity
C. availability
D. complexity
Correct Answer: B
QUESTION 3
How is confidentiality defined in the CVSS v3.0 framework?
A. confidentiality of the information resource managed by person due to an unsuccessfully exploited vulnerability
B. confidentiality of the information resource managed by a person due to a successfully vulnerability
C. confidentiality of the information resources managed by a software component due to a successfully exploited
vulnerability
D. confidentiality of the information resource managed by a software component due to an unsuccessfully exploited
vulnerability
Correct Answer: C
QUESTION 4
Which Cyber Kill Chain Model category does attacking a vulnerability belong to?
A. Exploitation
B. Action on Objectives
C. Installation
D. Delivery
Correct Answer: A
QUESTION 5
Which of the following is the team that handles the investigation, resolution, and disclosure of security vulnerabilities in
vendor products and services?
A. CSIRT
B. ICASI
C. USIRP
D. PSIRT
Correct Answer: D
QUESTION 6
When incident data is collected, it is important that evidentiary cross-contamination is prevented. How is this
accomplished?
A. by allowing unrestricted access to impacted devices
B. by not allowing items of evidence to physically touch
C. by ensuring power is removed to all devices involved
D. by not permitting a device to store evidence if it is the evidence itself.
Correct Answer: D
QUESTION 7
Which CSIRT category provides incident handling services to their parent organization such as a bank, a manufacturing
company, a university, or a federal agency?
A. internal CSIRT
B. national CSIRT
C. coordination centers
D. analysis centers
E. vendor teams
F. incident response providers
Correct Answer: A
QUESTION 8
What is a listening port?
A. A port that remains open and waiting for incoming connections
Correct Answer: A
QUESTION 9
Refer to the exhibit.
» Read more about: Latest Cisco CCNA Cyber Ops 210-255 exam Dumps Practice Test – Micvce »