Get the latest Cisco CCNA Security 210-260 dumps pdf practice materials and dumps vce youtube update free demo. High quality leads4pass 210-260 dumps exam training resources free update. “Implementing Cisco Network Security” is the name of Cisco CCNA Security https://www.leads4pass.com/210-260.html exam dumps which covers all the knowledge points of the real Cisco exam. leads4pass 210-260 dumps Cisco CCNA Security exam questions and answers are updated (310 Q&As) are verified by experts. The best Cisco CCNA Security 210-260 dumps pdf practice files and study guides free try, pass Cisco 200-105 exam test easily.
Latest leads4pass 210-260 dumps pdf materials free download from google drive: https://drive.google.com/open?id=0B_7qiYkH83VRcnI0SE83bHBvQ1k
Latest leads4pass 210-255 dumps pdf materials free download from google drive: https://drive.google.com/open?id=0B_7qiYkH83VRTTJsYkV3c2xZb2s
Vendor: Cisco
Certifications: CCNA Security
Exam Name: Implementing Cisco Network Security
Exam Code: 210-260
Total Questions: 310 Q&As
QUESTION 1
Which feature of the Cisco Email Security Appliance can mitigate the impact of snowshoe spam and sophisticated phishing attacks?
A. contextual analysis
B. holistic understanding of threats
C. graymail management and filtering
D. signature-based IPS
Correct Answer: A
QUESTION 2
When a company puts a security policy in place, what is the effect on the company’s business?
A. Minimizing risk
B. Minimizing total cost of ownership
C. Minimizing liability
D. Maximizing compliance
Correct Answer: A
QUESTION 3
Which EAP method uses Protected Access Credentials?
A. EAP-FAST
B. EAP-TLS
C. EAP-PEAP
D. EAP-GTC
Correct Answer: A
QUESTION 4
Which tasks is the session management path responsible for? (Choose three.)
A. Verifying IP checksums
B. Performing route lookup
C. Performing session lookup
D. Allocating NAT translations
E. Checking TCP sequence numbers
F. Checking packets against the access list
Correct Answer: BDF
QUESTION 5
What is the purpose of the Integrity component of the CIA triad?
A. to ensure that only authorized parties can modify data
B. to determine whether data is relevant
C. to create a process for accessing data
D. to ensure that only authorized parties can view data
Correct Answer: A
QUESTION 6
Which Cisco product can help mitigate web-based attacks within a network?
A. Adaptive Security Appliance
B. Web Security Appliance
C. Email Security Appliance
D. Identity Services Engine
Correct Answer: B
QUESTION 7
Refer to the exhibit.
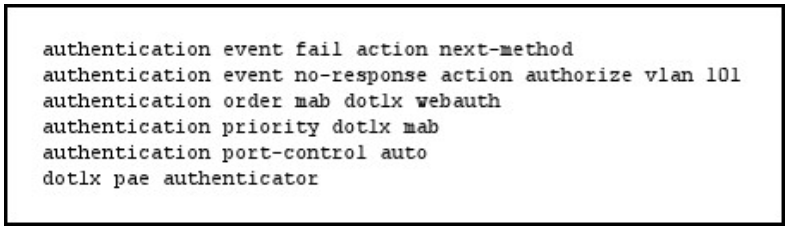
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
A. The supplicant will fail to advance beyond the webauth method.
B. The switch will cycle through the configured authentication methods indefinitely.
C. The authentication attempt will time out and the switch will place the port into the unauthorized state.
D. The authentication attempt will time out and the switch will place the port into VLAN 101.
Correct Answer: A
QUESTION 8
What security feature allows a private IP address to access the Internet by translating it to a public address?
A. NAT
B. hairpinning
C. Trusted Network Detection
D. Certification Authority
Correct Answer: A
QUESTION 9
What is one requirement for locking a wired or wireless device from ISE?
A. The ISE agent must be installed on the device.
B. The device must be connected to the network when the lock command is executed.
C. The user must approve the locking action.
D. The organization must implement an acceptable use policy allowing device locking.
Correct Answer: A
QUESTION 10
What is the purpose of a honeypot IPS?
A. To create customized policies
B. To detect unknown attacks
C. To normalize streams
D. To collect information about attacks
Correct Answer: D
QUESTION 11
In which three ways does the RADIUS protocol differ from TACACS? (Choose three.)
A. RADIUS uses UDP to communicate with the NAS.
B. RADIUS encrypts only the password field in an authentication packet.
C. RADIUS authenticates and authorizes simultaneously, causing fewer packets to be transmitted.
D. RADIUS uses TCP to communicate with the NAS.
E. RADIUS can encrypt the entire packet that is sent to the NAS.
F. RADIUS supports per-command authorization.
Correct Answer: ABC
QUESTION 12
Which statement about extended access lists is true?
A. Extended access lists perform filtering that is based on source and destination and are most effective when applied to the destination
B. Extended access lists perform filtering that is based on source and destination and are most effective when applied to the source
C. Extended access lists perform filtering that is based on destination and are most effective when applied to the source
D. Extended access lists perform filtering that is based on source and are most effective when applied to the destination
Correct Answer: B
Read more: https://www.leads4pass.com/210-260.html dumps exam questions and answers free update, leads4pass 210-260 dumps Cisco pdf training resources and study guides free try, 100% success and guarantee to pass.
Latest leads4pass 210-260 dumps vce youtube update free demo: https://youtu.be/seDmEyXcd3w