
Candidates can use New update CCNP Security 350-701 dumps with PDF and VCE: https://www.leads4pass.com/350-701.html (562 Q&A), and successfully pass the “Implementing and Operating Cisco Security Core Technologies (SCOR)” exam.
The new Update 350-701 Dumps covers virtually all exam content for the complete implementation and operation of core security techniques: Network security, Cloud security, Content security, Endpoint protection and detection, Secure network access Visibility, and enforcement.
Download the free CCNP Security 350-701 PDF:https://drive.google.com/file/d/1DATVJjpi0ElO_GWcQRr2TVnWpa_sgSdu/
Read the free CCNP Security 350-701 exam questions and answers online:
| Number of exam questions | Exam Name | From | Release time | Previous issue |
| 13 | Implementing and Operating Cisco Security Core Technologies (SCOR) | leads4pass | Nov 15, 2022 | 350-701 dumps questions |
NEW QUESTION 1:
How does Cisco Umbrella archive logs to enterprise-owned storage?
A. by using the Application Programming Interface to fetch the logs
B. by sending logs via Syslog to an on-premises or cloud-based Syslog server
C. by the system administrator downloading the logs from the Cisco Umbrella web portal
D. by being configured to send logs to a self-managed AWS S3 bucket
Correct Answer: D
Reference: https://docs.umbrella.com/deployment-umbrella/docs/manage-logs
NEW QUESTION 2:
An administrator is configuring NIP on Cisco ASA via ASDM and needs to ensure that rogue NTP servers cannot insert themselves as the authoritative time source Which two steps must be taken to accomplish this task? (Choose two)
A. Specify the NTP version
B. Configure the NTP stratum
C. Set the authentication key
D. Choose the interface for syncing to the NTP server
E. Set the NTP DNS hostname
Correct Answer: CE
NEW QUESTION 3:
Refer to the exhibit.

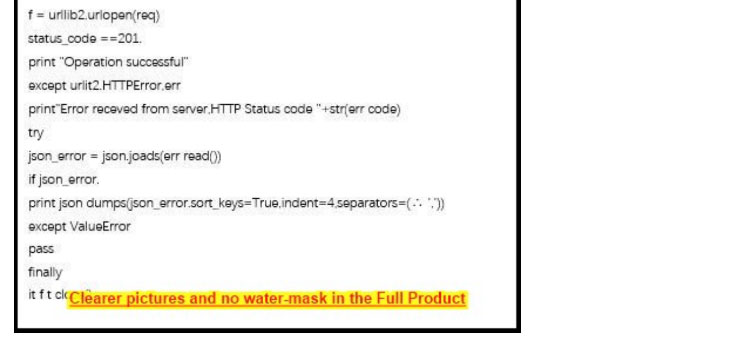
What is the function of the Python script code snippet for the Cisco ASA REST API?
A. adds a global rule into policies
B. changes the hostname of the Cisco ASA
C. deletes a global rule from policies
D. obtains the saved configuration of the Cisco ASA firewall
Correct Answer: A
NEW QUESTION 4:
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network.
What must be configured, based on a predefined threshold, to address this issue?
A. Bridge Protocol Data Unit Guard
B. embedded event monitoring
C. storm control
D. access control lists
Correct Answer: C
ExplanationStorm control prevents traffic on a LAN from being disrupted by a broadcast, multicast, or unicast storm on one of the physical interfaces.
A LAN storm occurs when packets flood the LAN, creating excessive traffic and degrading network performance. Errors in the protocol-stack implementation, mistakes in network configurations, or users issuing a denial-of-service attack can cause a storm.
By using the ” storm-control broadcast level [falling-threshold]” we can limit the broadcast traffic on the switch.
NEW QUESTION 5:
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to network resources?
A. BYOD onboarding
B. Simple Certificate Enrollment Protocol
C. Client provisioning
D. MAC authentication bypass
Correct Answer: A
NEW QUESTION 6:
Refer to the exhibit.
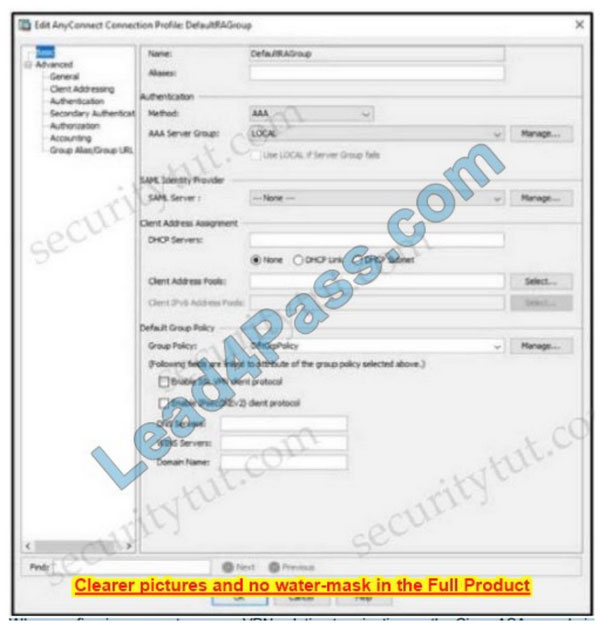
When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine certificates.
Which configuration item must be modified to allow this?
A. Group Policy
B. Method
C. SAML Server
D. DHCP Servers
Correct Answer: B
In order to use AAA along with an external token authentication mechanism, set the “Method” as “Both” in the Authentication.
NEW QUESTION 7:
Refer to the exhibit.
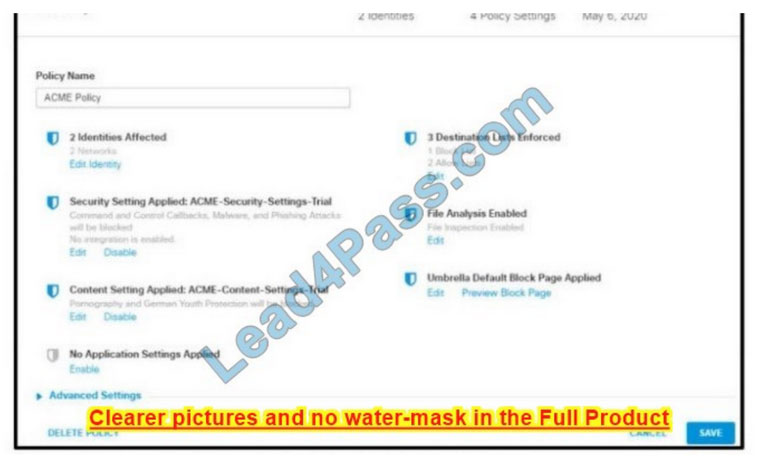
How does Cisco Umbrella manage traffic that is directed toward risky domains?
A. Traffic is provided through the intelligent proxy.
B. Traffic is managed by the security settings and blocked.
C. Traffic is managed by the application settings, unhandled and allowed.
D. Traffic is allowed but logged.
Correct Answer: B
NEW QUESTION 8:
What is the purpose of CA in a PKI?
A. To issue and revoke digital certificates
B. To validate the authenticity of a digital certificate
C. To create the private key for a digital certificate
D. To certify the ownership of a public key by the named subject
Correct Answer: A
Reference: https://cheapsslsecurity.com/blog/understanding-the-role-of-certificate- authorities-in-pki/
NEW QUESTION 9:
What is the benefit of using Cisco Tetration?
A. It collects telemetry data from servers and then uses software sensors to analyze flow information.
B. It collects policy compliance data and process details.
C. It collects enforcement data from servers and collects interpacket variation.
D. It collects near-real-time data from servers and inventories the software packages that exist on servers.
Correct Answer: A
NEW QUESTION 10:
Which two fields are defined in the NetFlow flow? (Choose two)
A. type of service byte
B. class of service bits
C. Layer 4 protocol type
D. destination port
E. output logical interface
Correct Answer: AD
Cisco standard NetFlow version 5 defines a flow as a unidirectional sequence of packets that all share seven values which define a unique key for the flow:+ Ingress interface (SNMP ifIndex)+ Source IP address+ Destination IP address+ IP protocol+ Source port for UDP or TCP, 0 for other protocols+ Destination port for UDP or TCP, type and code for ICMP, or 0 for other protocols+ IP Type of
ServiceNow:
A flow is a unidirectional series of packets between a given source and destination.
NEW QUESTION 11:
An organization wants to secure data in a cloud environment. Its security model requires that all users be authenticated and authorized.
Security configuration and posture must be continuously validated before access is granted or maintained to applications and data.
There is also a need to allow certain application traffic and deny all other traffic by default.
Which technology must be used to implement these requirements?
A. Virtual routing and forwarding
B. Microsegmentation
C. Access control policy
D. Virtual LAN
Correct Answer: B
Zero Trust is a security framework requiring all users, whether in or outside the organization\’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data.
Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.
The Zero Trust model uses micro-segmentation — a security technique that involves dividing perimeters into small zones to maintain separate access to every part of the network — to contain attacks.
NEW QUESTION 12:
Which two characteristics of messenger protocols make data exfiltration difficult to detect and prevent? (Choose two)
A. Outgoing traffic is allowed so users can communicate with outside organizations.
B. Malware infects the messenger application on the user endpoint to send company data.
C. Traffic is encrypted, which prevents visibility on firewalls and IPS systems.
D. An exposed API for the messaging platform is used to send large amounts of data.
E. Messenger applications cannot be segmented with standard network controls
Correct Answer: CE
NEW QUESTION 13:
What is the purpose of the My Devices Portal in a Cisco ISE environment?
A. to register new laptops and mobile devices
B. to request a newly provisioned mobile device
C. to provision userless and agentless systems
D. to manage and deploy antivirus definitions and patches on systems owned by the end-user
Correct Answer: A
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2- 4/mydevices/b_mydevices_2x.html
…
Download the above CCNP Security 350-701 exam questions and answers:https://drive.google.com/file/d/1DATVJjpi0ElO_GWcQRr2TVnWpa_sgSdu/
New update CCNP Security 350-701 dumps have been verified to be real and effective, and 562 newly updated exam questions cover the complete 350-701 SCOR certification exam. Candidates click here for the latest 350-701 dumps https://www.leads4pass.com/350-701.html online to ensure they pass the 350-701 SCOR Certification Exam.